FAQ Cyber Check
- What is Cyber Risk?
Cyber risk is much more than just hacking. It involves internal and external risks, product risk, third-party risk and aggregate risk, such as service provider and supplier failure, human error, software obsolescence, and upstream internet and network interruptions.
- Who can be involved in a cyber-attack?
The cyber risk ecosystem is complex and involves many players and aspects. Organisations of all sizes have been or will be impacted by cyber risks, and whilst this threat is well publicised, it is not always well understood. All businesses are connected to the internet: emailing customers, searching the internet, or paying suppliers are just some of the ways businesses interact online.
- Is it possible to identify cyber risk before a cyber-attack, data breach or business interruption happens?
Unfortunately, many businesses are still unprepared to manage cyber risk and understand their vulnerabilities. In this age of digital disruption, there is a clear need for businesses to look out for cyber threats on an ongoing basis. Recognising this need, CRIF has developed CRIF Cyber Check Report, a proactive response to cyber management in 3 simple steps.
- What is the Cyber Check Report?
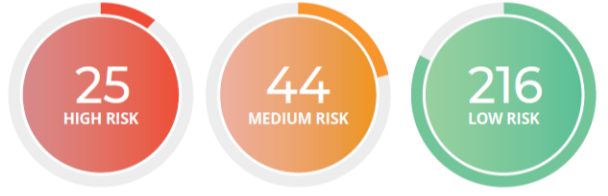
High priority risks are flagged for immediate action.
No technical expertise is required.
Identify vulnerabilities to take corrective action.
CRIF CYBER CHECK is simple and easy to use. A cost-effective proactive response to cyber risk management The report provides a summary of your organization's current cybersecurity posture with influencing risk factors.
- How can I use this Cyber Check Report?
- Knowing your cybersecurity risk today lets you see how attackers can target your organization’s critical assets, which could lead to data loss.
- You can Further Check Discreetly on your Partners.
- What can I expect from this Cyber Check Report?
- Access a snapshot report of your current security framework for a limited time.
- Know what the findings are and what they mean to your risk across multiple domains
- Learn how your organization's cybersecurity performance compares to your peers
- Learn how to use your categorized risk to influence corrective action with risk prioritized data based on issue severity.
